

False rumors or a few too many Friendship Page URLs from a contact with CFD (Compulsive Forwarding Disorder) can be annoying at times, but there is never any real danger. In the past, the few ICQ related "hacking" programs were also not much more than an annoyance. But recently there have been some new programs appearing on the net that can, under the right conditions, pose a very real threat to you or your computer, particularly Windows 95 & 98 (oxymoron words of the day: Windows security). So it is time to explain some of the hazards facing the ICQ community and how to protect yourself from becoming a victim. Your #1 defensive weapon: knowledge.
Imagine one day you log on to ICQ and instead of the usual dozen or so messages from your friends, you are greeted with hundreds, possibly thousands of flashing messages from UINs you have never seen before. One of three things has probably just happened: 1. You have become incredibly popular and everyone wants to talk to you. Unless you just won the lottery by playing your UIN, this is probably not the case. 2. All the messages that were sent to you in the past year but never got through have all shown up at once. This is also unlikely. 3. Opening a few of the messages you find that they are all the same, either garbled text or a message (most likely obscene). Buddy, you've been bombed. ICQ bombing programs (sometimes also referred to as flooders, but different from a packet flooder) are a close cousin to e-mail bombing programs. With the latter, someone can enter your e-mail address into a program that will send hundreds or even thousands of e-mails to you. With the ICQ equivalent, your UIN has been entered and a flood of messages sent to you. Some ICQ bomber programs go through the Mirabilis web page while others can send messages directly to you. In either case, it could take hours to close out all the messages by hand. And since some bomber programs can make the messages appear to have come from many random UINs, your ignore list isn't going to prevent the next attack. So what can you do about these attacks? Well, the number one best way to prevent this and everything else described on this page is: don't piss people off. Seriously, while there are malicious people who will attack just to be jerks, many of the people who become victims probably provoked the attack in some way. Because ICQ allows people to remain anonymous, it leads some folks to get very bold and obnoxious. They think that since no one knows who they are they are safe. Then one day they piss off the wrong person and get a rude awakening. Just treat people you meet on the net with respect and courtesy and you can avoid a lot of grief. But sometimes you could be the victim of an unprovoked attack. In that case there are a few precautions you can take. First, make sure your ICQ is in Advanced Mode. Then click on the ICQ button and go to the Security & Privacy menu. Select the Ignore List tab along the top and you will see a menu (like the one shown below) with several check boxes. This is where you would normally add someone who is giving you trouble to your Ignore List, thus blocking messages from them. But there are a few other features on this menu that can help prevent message bombing. The first option you can check is Accept messages only from users on my contact list. While checking this box will limit the number of people who can contact you to only those you have on your list, it will also prevent a flood of messages from random UINs, unless one of the random UINs happens to match a person on your list (odds are that won't happen often). You'll also see check boxes for Do not accept WWPager messages and Do not accept EmailExpress messages. While these are not used as often for bombing, they can be so you may want to consider checking them as well. While you are on this menu, you can also check Do not accept MultiRecipient Message from either All Users or Users not on your contact list. This won't prevent bombing, but it will block those forwarded URLs and messages that some people like to send to all or most of the contacts on their list. If you really don't like that stuff then this is the box for you. 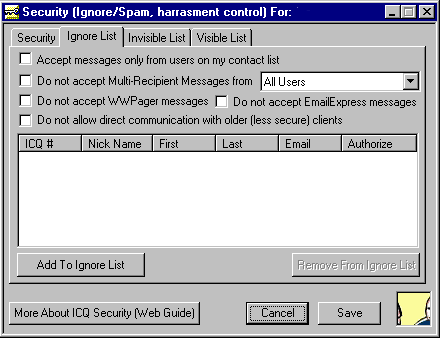 Keep in mind that checking all those boxes will mean only people on your contact list can send you messages. If you have an ICQ contact panel on your website you won't be able to receive messages from it. Unless you have been bombed or think you are at risk, it might be better to leave those boxes unchecked. If you are bombed, there are several small utility programs that will remove all unread messages automatically, saving you the trouble of closing them yourself. [Edit: Programs removed due to being out of date.]
Spoofing is pretending to be someone else. Like bombing, it began with e-mail and is now being done with ICQ messages. A spoofed message may be sent to either masquerade as someone else or to hide the true identity of the sender. It could be done as a prank or with truly evil intent. While it poses no danger to your computer, it could lead to some embarrassing situations if you are tricked into believing that the message(s) are really from the person they appear to be. It is for this reason that I've included them here, so you'll know that if you receive a really unusual message from someone it may not be from them at all. Or maybe is was from them and they were just really drunk at the time. *g* While it is quite easy to spoof an ICQ message, it is not the same as taking over someone's account. The main difference is that the spoofer can only send messages as someone else, they can't receive that person's messages without having access to their account (usually that would require knowing their password). So if you get a strange message from someone but they don't respond to your messages (or they have no idea what you are talking about), then the message may have been spoofed. Just use some common sense and don't be too quick to jump to conclusions. Update: There is now a spoof program than not only can masquerade as someone else, but can also receive messages that are sent back. That doesn't mean it can get into someone's ICQ account and intercept all their messages, just the responses to the spoofed messages that are sent online. Still, the ability to carry on a two-way conversation as someone else can lead to some real problems and you should be very careful about discussing sensitive subjects. While we are on the subject of new programs, there is another that can potentially grab your password, but you have to "help" a little. The way this program works is it pretends to be a Mirabilis server, and if you try to log into it your password will be recorded. But before you log in, someone has to convince you to add the IP address for their "server" and then have you disconnect from Mirabilis and connect to them. This isn't that difficult to do, many people add new servers to their ICQ client having been told they would "never lose their connection again." I should mention that this isn't true, when the ICQ network is having problems, it doesn't matter how many servers you have on your list, they will all be having the same troubles. Also, if the cause of your disconnects is your ISP or the path your data is taking across the Internet to the Mirabilis server, again having more servers won't solve the problem. But I digress. Many people add new servers to their list, and if one of them happens to be a spoofed server and you log into it, you have just compromised your password and potentially your account. For what it's worth, I've tried a lot of different server combinations and these four seem to work as well (or better) than adding a dozen: icq.mirabilis.com - 4000 icq1.mirabilis.com - 4000 icq2.mirabilis.com - 4000 icq3.mirabilis.com - 4000 So my advice is if someone gives you a server addy in the form of an IP address (eg. 209.86.184.214) and tells you to log off ICQ and then back in to that "server"... you would be better off saying "no thank you."
Nuking programs come in two varieties, those that attack ICQ and those that attack your operating system. In either case, something is going to crash and if it happens often enough it can become really annoying. One of the earilest ICQ nukers was called ICQ Shutdown, and that's all it did was shutdown ICQ, which would then have to be restarted. To attack someone's ICQ (or anything else), the victim's IP address must be known. Before moving on, let's discuss IPs in a little more detail. A unique IP address is assigned to each computer connected to the Internet. In the case of most dial-up accounts, the IP address will be assigned from a pool of addresses allocated to an ISP. The IP address you are assigned may be different each time you log on, this is called a dynamic IP. Often to find the target of an attack, the IP address must be known. But since it changes with each log-on, knowing what someone's IP was yesterday is of no value (unless they have remained online since then). Older versions of ICQ used to display everyone's IP addy in the User Info menu, and that could be dangerous. So the latest version of ICQ allows you to hide your IP addy (look at the Security & Privacy menu and choose the Security tab, then look for the IP Hiding and check the box next to where it says Do not allow others to see my IP address). There is just one problem with this that you need to be aware of. ICQ messages are sent from IP to IP when sent to someone who is online (ie. not through an ICQ server). For the other person's ICQ to be able to send a message back to you, it has to know your IP addy, even if it isn't displayed. That's where the problem arises, it is possible to patch (ie. modify the ICQ program's code) to display the "hidden" IP address, regardless of whether your ICQ program tells their ICQ program to hide it or not. This opens up a potential security hazard and there is nothing that the programmers at Mirabilis can do about it short of having all messages go through one of their servers, which is impractical. So be aware that the moment you accept a chat request or respond to a message, you could be giving away your computer's location (IP) on the net. Which brings us back to nuking programs. Once someone can "find" your computer, they need to know one more piece of information, the "port" your ICQ program is listening on. Ports are another form of electronic address through which data is passed. There are thousands of possible ports that can be used. ICQ usually opens a port in the 1000 to 2000 range. Many nuking type programs will "sniff" each port looking for ICQ, and when they find it, that is when the nasty business starts. Hackers who study (ie. disassemble) the ICQ code occasionally find flaws and then devise ways to exploit those flaws. Typically they find that if data is sent in a particular form it will cause ICQ to crash or freeze-up. Usually this won't cause any permanent damage, but it sure can be irritating to be in the middle of a chat and have your ICQ crash. Sometimes just running ICQ again is all that is needed, other times you may have to reboot your system. Remember that I said nuking programs came in two varieties, one that attacked ICQ and the other that attacked your operating system? The attacks on your operating system can be more serious. Typically the result of such an attack is the dreaded "blue screen of death" or a complete lock-up of your system. The only way to correct this condition is to reboot, which in turn may require a scan disk. If you had any unsaved files open they could be lost, though usually, as with the ICQ attacks, there will be no permanent damage. Just the same, depending on the speed of your system, it could take about five minutes to recover and log back on, at which time your nemesis can start the process of hunting down your new IP for the next attack. So once again the question arises, what can be done about this? In the case of ICQ attacks, the best thing you can do is stay current. First look at the version number of your copy of ICQ (click the ICQ button, then Help and then About, the version should look something like ICQ Version 98a Beta, Dll 1.30). Next check the Mirabilis site or Download.Com to see what the latest version is. If you don't have it, then get it. I've heard people say they don't want to bother getting the latest version because it doesn't appear to have any new features that would make it worth the effort to download and install. But new features usually only appear in major version updates (like going from version 1.113 to 98a). These minor changes are called "maintenance releases." Usually they consist of bug fixes and security patches. You may be able to get along just fine with an older version, until someone starts attacking you. The flaw that they are exploiting may have been fixed in the most recent version, so I generally try to stay current, even if I'm not having any problems. This is a good idea with most communications type programs such as browsers and e-mail clients. That doesn't mean always getting the beta releases (in the case of ICQ they are all beta releases), but the most recent public release... unless of course you enjoy beta testing new products. In that case you can be the first one on your block (to crash, usually *g*). I should note that there is one other method that is sometimes used to thwart attacks. Software is available that will open additional ports (14 in the case of ICQ Protector) in the same range that ICQ uses. This makes it difficult for a would be attacker to determine which port is being used by ICQ, and which are decoys. I haven't tried this software, but in theory it should force an attacker to work overtime trying to find the correct port, though it won't stop a determined attacker. For operating systems like Windows95 and 98, you can check with Microsoft for the latest patches, or Windows Internet Patches or WinFiles.Com for a list of links to the patches. Whether it is ICQ or Windows, it seems like every few months there is a new patch or version available, and not long after that a new exploit is found and the process starts over again. I've just come to accept that as part of life in the computer age. Eventually we'll be seeing software that updates itself, "calling home" every time it is run to see if a new version is available. Occasionally you may get a message when ICQ connects saying that a new version is available and asking if you would like to upgrade. Take a hint, what they are saying is "we found a problem with the old version and fixed it." Under no circumstances will a Mirabilis employee contact you directly and ask if you would like to be sent the latest version of ICQ from him or her. That is not the way they or most other companies work, which brings us to our next topic.
Not all threats to your system are technical in nature. A smooth talker can get all the info they need to break into your system or steal your ICQ account without ever running a hacker program. A typical ploy is to be contacted by someone claiming to be an employee of Mirabilis. Their ICQ info may even say something like "Mirabilis Tech Support" and have a Mirabilis e-mail address. That means nothing, anyone can start an account and put in deceptive info (do a search with "Mirabilis" for the Nickname and see how many you turn-up... you can even misspell it "Miribilis" and get a hit for "tech support"). Many Mirabilis employees do have ICQ accounts, but they won't contact you with some story about how they need you to tell them your password. If they really needed to know they could find it without having to ask you, that information is stored on their servers. It is a cardinal rule of security that no one belonging to an organization to which you hold a password will ever ask for it. More likely you will lose or forget your password and end up asking them. This not only applies to Mirabilis, but your ISP and anywhere else you may have a password. Yet everyday there are people who get stupid when confronted by someone sounding authoritative and demanding to know their password. A potentially worse scam involves asking if you would like to beta test the latest version of ICQ. The "representative" from the company will tell you all about this great program with incredible new features. Just when you are about to start drooling in anticipation of taking this puppy for a test drive, they will tell you that first they have to verify your age, and to do that they'll need to know your credit card number, the name on the card and the expiration date. If you foolishly hand it over, that will probably be the last you ever hear from them, though you may be reminded of what a sucker you were when your next statement arrives. There have probably been more computer security systems compromised by sheer force of will than any form of number crunching. That's not surprising when you consider that the human mind can be the most powerful computer that exists, just make sure yours is switched into the on position the next time someone starts asking a lot of questions about things they have no business knowing.
I've saved the best (or worse) for last. A "back door" is a way for someone to circumvent the usual security of a computer system and gain access, perhaps even control, without the legitimate user(s) of the system even knowing. Of all the things that could happen to you, this can be the most disastrous. Not only can someone destroy all your vital data, but they can read and steal it as well. Anything you can access, so can they. Do your banking or investing by computer? Perhaps you have shopping or gambling accounts? Well so will the person secretly controlling your computer. Do you have any intimate details of your life stored on your computer? They may not remain intimate, you could even find yourself being blackmailed. There are three programs I have seen that are capable of opening back doors. The first is called ICQ Trogen (a play on the word "trojan"). It consists of two programs, icqtrogen.exe (the server) and icqclient.exe (the client). The trick is to find a way to get someone to rename their icq.exe as icq2.exe and then rename icqtrogen.exe as icq.exe. In effect that means when the ICQ NetDetect program tries to run ICQ, it will run the renamed ICQ Trogen program instead, which in turn will run ICQ so the victim doesn't get suspicious. Once ICQ Trogen is running quietly in the background, the remotely located hacker runs the client software. All they need to know is the victim's IP address, and with the help of a patched version of ICQ, that may be an easy thing to find out. Once the client software has contacted the server (ie. trogen), the hacker will be able to issue commands to upload, download, execute and list files on the remote computer. Unless the victim notices unusual hard drive or modem activity, they may have no clue about what is happening in the background, especially if they are one of those people who likes to stay connected to the net 24/7, even when they are away at work or sleeping. That little N/A (Extended Away) icon on ICQ can be like a calling card to hackers who wish to access a computer undisturbed. But what about the trick of getting the server software set-up on the remote computer? That's where the help of a Dropper program and some social engineering comes in. Dropper programs were originally created to attach a virus (which is just another type of program) to a host program. The host can be any executable program. In this case with a little tweaking, the Dropper can not only attach the Trogen file, but also include some set-up code to rename the existing icq.exe file and then plant trogen in its place. All that is left to do is find a tempting enough host file and a plausible excuse to get the victim to run it. That usually turns out to be the easiest part, just send someone an executable greeting card on their birthday and you're in like Flint. (I bet some of the friends I've sent executable greeting cards to lately are getting a bit nervous at this point. Don't worry, I haven't been using you as test subjects. Honest. I swear it. J ) The next back door program I've seen is a little different. It's called ICKiLLeR and it is not supposed to be a back door at all. In fact, its stated purpose is to act as an ICQ nuker, but guess what? The programmers wrote a little back door into it for their own private use. Hacking the hackers, you gotta love it (unless of course you are one of the people who installed this little gem). I won't go into any more detail about this one, except to say if you installed a program to mess with other people and you turn out to be the victim, well... that's called poetic justice. The final program is not ICQ specific, in fact it can function quite well without ICQ. But as we've seen, since it is necessary to know the IP address of the victim and when they are online, ICQ can be a valuable tool in a hacker's arsenal. On August 3rd, 1998, the Cult of the Dead Cow (cDc) released a free program called Back Orifice (BO). It is billed as a "remote Windows 9x administration tool" and in fact that is exactly what it is. Once installed on a host computer running Windows 95 or 98, BO will allow its remote operator to (and I quote from their website): System control: Create dialog boxes with the text of your choice. Log keystrokes. Lockup or reboot the machine. Get detailed system information, including: current user, cpu type, windows version, memory usage, mounted disks (including hard drives, cdroms, removable drives and remote network drives) and information for those drives, screensaver password, passwords cached by the user including those for dialups, web and network access, and any other password cached by the operating system. File system control: Copy, rename, delete, view, and search files and directories. File compression and decompression. Process control: List, kill, and spawn processes. Registry control: List, create, delete and set keys and values in the registry. Network control: View all accessible network resources, all incoming and outgoing connections, list, create and delete network connections, list all exported resources and their passwords, create and delete exports. Multimedia control: Play wav files, capture screen shots, and capture video or still frames from any video input device (like a Quickcam). Packet redirection: Redirect any incoming TCP or UDP port to any other address & port. Application redirection: Spawn most console applications (such as command.com) on any TCP port, allowing control of applications via a telnet session. HTTP server: Upload and download files on any port using a www client such as Netscape. Integrated packet sniffer: Monitor network packets, logging any plaintext passwords that pass. Wow, that's one helluva "remote administration tool." And it's no joke. The program was demonstrated at DEF CON 6.0 and has been tested by numerous organizations, PC Week Labs among them. This is the real deal, folks. According to the cDc, during the first month that the program has been available, there have been over 100,000 downloads. Meaning that not only does it work, but a lot of people are getting a copy. But wait, there's more. In addition to the built-in functionality, it can also run "plug-ins" in the form of DLL files. That gives the program almost unlimited potential. As of this writing (Sept. '98), there are only a few plug-ins publicly available, but considering that BO has only been publicly available itself for a month, this small collection is impressive. Remember the Dropper programs? There are two available for BO. The first was a quickie called Saran Wrap that could package BO with a small collection of harmless looking files. Next came Silk Rope, a more elegant dropper/binder. With Silk Rope, the BO server (the program that runs on the target/host computer, perhaps yours?) can be combined with any executable file (think birthday greeting card again). The BO server is only 125Kb (about 160Kb with installation code), so it doesn't add much to the original executable. Along with BO, a plug-in can also be binded to the EXE. One of the plug-ins is called Butt Trumpet. Keep in mind that once an executable file with BO piggybacking on it gets turned loose on the net, there is no predicting where or on how many computers it could find itself making a home. In order to control BO, the remote operator first has to find where the program has taken up residence. That's where Butt Trumpet comes in, it allows BO to phone home by sending a covert e-mail to a predetermined address (an anonymous remailer if the person setting it up has any sense and doesn't want to make it easy to be tracked down). Once the remote operator gets the "here I am" e-mail with the host's IP addy, he is ready to make contact and take control. There is an even more sophisticated way of tracking where BO lands and when the server is available to do its master's bidding by using a plug-in called Speakeasy. Unlike Butt Trumpet which is a one shot deal, Speakeasy is an invisible IRC client for BO. Once running, it will attempt to log into a predetermined IRC channel with the name "BO_" followed by 6 random letters. It then proceeds to broadcast to the group its host's IP address every two minutes. In this way, a number of BOs could be monitored for the current IPs of their hosts. In theory, the remote operator(s) monitoring the IRC channel could choose from dozens of computers to command through a legion of BOs. Think of it as being like an ICQ list, only instead of chatting with people when they log on, you start talking directly to their computers without them knowing it. So what can someone do once they get into a BO controlled computer? Pretty much anything the legitimate user can do. Thanks to Microsoft's loose security with Win95 and 98, BO could easily pick-up and report back plain text cached passwords, like a dial-up account or screensaver. BO also can log all keystrokes the user types and then upload the log file to the remote operator. In time that could reveal additional passwords, credit card info... anything typed into a window. Screen shots can be taken and saved as bitmaps, compressed and then retrieved. Any file on the system could be downloaded or new files could be sent to the target computer and run at will. Of course in addition to spying, the remote operator could also toast the user's hard drive and cover his own tracks in the process. Are you feeling just a little bit uncomfortable at this point? Well, Microsoft would like to assure you that BO doesn't pose a real threat to you as long as you follow a few simple precautions (quotes in italics from a Microsoft press release about BO): The computer is connected to the Internet through an Internet service provider that dynamically assigns IP addresses - as the vast majority of ISPs already do. Oh sure, that will work... not! We've already seen how many ways there are to obtain the target computer's IP. In addition, the BO client software has an IP scanning feature, if you know what ISP the victim is using then you can scan the range of IPs allocated to that ISP. The BO client knocks on each IP asking "are you there" until it gets a response from a BO server. So much for dynamic IPs being a defense. The computer is on a network with a firewall or proxy server between it and the attacker. First it is questionable just how well a firewall could block communication with BO since standard UDP and TCP protocols are being used. But even if I grant Microsoft this one, it doesn't do most of us any good because we are not insulated behind firewalls or proxy servers. The computer is not connected to the outside world. Well, they are right about this one, as long as we never log on to the net again we'll be safe. Great solution, Microsoft, let's just shut the Internet down and play Windows Solitaire all day. I can see how "Microsoft takes security seriously." Of course BO has to get into your system before anything can happen. Microsoft also has some advice on how not to allow this to occur: Clearly, users should prevent this installation by following good practices like not downloading unsigned executables. Oh, now I get it, we should only download executable files from sites with secured servers and certificates. In other words, only get your software from big corporate sites like... Microsoft. Yes I'm sure they would consider that a very good practice indeed. I wish more sites could afford server certificates, but not everyone with a program to offer can cover the additional cost. It isn't practical for most of us to limit where we "want to go today" to Microsoft and a handful of other major vendors. So much for Microsoft helping us with this problem, they are following their usual pattern of burying their head in the sand and denying there is a threat. What little advice they do offer is useless for most of us. The root of the problem with Win95/98 is that it was never intended to be a networked operating system like WinNT. Basically Microsoft designed a car and when they found out we wanted to fly, instead of building a plane they glued wings on the car. Now they expect us to drive over the edge of a cliff... where do you think you're going today? I'll now attempt to be a little more helpful than the geniuses in Redmond. First, be aware that a threat does exist. That is the whole point of why I've described BO in such detail, so you'll know what you are up against and take it seriously. There are three things you need to know: how BO can get into your system, how to detect it if it does get in and how to get rid of it once detected. We've already seen how BO gets in, it can piggyback its way in on any executable file. You might ask "how is this different than a virus?" One difference is that unlike a virus, once BO is in your system it won't try to attach itself to any other files. That is both good and bad. It's good that it won't automatically try to spread, though once a remote operator has control of your system they could start swapping some of your more frequently traded executables with BO "enhanced" versions. It is also possible for some hacker to write a new delivery program that would attempt to infect other files, I just haven't seen that yet. The bad part is that once BO is in place, it deletes its install file and tries to cover its tracks, thus making it a little bit harder to detect. But BO differs from a virus in one other crucial area: the reason someone would want to place it on your system. A typical virus can either play a little joke on you (not very funny, IMHO) or destroy your data. Most people have nothing to gain from sending out a virus, so why bother? But BO offers some enticing possibilities for spying on your "friends," checking up on your boy/girlfriend, keeping tabs on business associates or competitors, high tech crime or good old fashioned blackmail. And it doesn't have to be aimed at people you personally know, once it starts to spread the creator can begin to "farm" dozens of computers for "useful" data. When the BO server is configured, a password can be added so that it will only communicate with remote clients that also know the password, thus creating a "private network" of BO owned computers. The point is, where someone would have no motive to spread a virus, BO could be very tempting. Thus your chances of being exposed to it are much greater, as is the potential damage. At least once a virus detonates, you are aware of the problem and at worst compromised your data and perhaps infected your friends. But if BO goes undetected, someone could poke around inside your computer for months, even years. So how do you detect BO? Well, it isn't easy without some software to assist you. BO operates in the background, it won't appear on your taskbar and pressing ctrl-alt-del won't bring it up on the task list. The actual server file can be given any name and hidden in your Windows system directory, good luck trying to spot it. In the original executable file that delivered BO the code is encrypted, thus making it difficult (though not impossible) for a virus scanner to pick-up on BO prior to its installation. The first clue you may have that someone is poking around in your system is unusual hard drive and modem activity... at least for people who pay attention to such things and don't leave their computer online while they are away for extended periods of time. Now don't go getting all paranoid just because your hard drive light occasionally comes on or you see your modem lights briefly flash. Depending on what software you have running, it isn't too unusual for your hard drive to be briefly accessed and if you are running ICQ it will "check-in" and cause your modem to periodically flash. But if you start to see continuous activity when you aren't doing anything, then it is time to get suspicious. If you see files being changed, moved, added or deleted then you either have a poltergeist or a hacker in your computer. And if a dialog window should unexpectedly open saying something like "Got ya, sucker!" then you better reach for the power switch, 'cause you are probably in deep, deep trouble. Before you get to that point, there are some precautions you can take. First, use your head and don't be too quick to run any executable file. This has long been good advice to prevent virus infections, but it goes double now. If someone wants you to run a program they sent, ask 'em where they got it from and then get it yourself from the original source. If it is from a reputable source like Download.Com or TuCows then it has probably been checked and is safe. If the file is from some temporary site like "HaPpY hAx0rZ" collection of questionable warez... well, roll the dice at your own risk. Listen carefully, do you hear that bugle sound? Could it be the cavalry of virus protection vendors charging in to save us? Maybe. There are already a few products available for detecting and eliminating BO. No doubt more are on the way. Also no doubt that the cDc and others will be writing new versions of BO and the dropper programs to defeat the detection software. Then the cycle will start again. One day the detection software eliminates BO, the next day a stronger BO eliminates the detection software. Charles Darwin would have loved it. UPDATE: As predicted, a new version of BO called Back Orifice 2000 was publicly released on July 22, 1999. BO2K features strong encryption, modular architecture that facilitates development of third party plug-ins and, unlike its predecessor, will run under Windows NT. The ability of BO2K to have its port setting configured (the original BO always used port 31337) will defeat many of the existing anti-trojan programs that specifically "listened" for BO on the default port. Also, there have been five variations of BO reported and three variations of the new BO2K. The "success" of BO has spawned at least a dozen other hidden "remote administrator" programs. I've tested a few and can tell you that not only do they work, but in some cases are very easy to use. With so many new backdoor programs being developed it bears repeating: don't run programs you didn't get from a reputable developer or distributor. UPDATE: In case BO isn't enough to worry about, meet BO's cousin NetBus. While NetBus appears to lack some of the sophisticated plug-ins that are available for BO, it is just as capable of opening a backdoor into your operating system. The two most common ways that NetBus is introduced into a victim's computer is via executable files called patch.exe and wackamole.exe. Note that these files can be renamed as anything and still deliver NetBus into your system. Patch.exe has been passed around as update for ICQ with a warning that the victim's ICQ would cease to function if they didn't run it. Wackamole.exe masquerades as a simple video game but installs NetBus the first time it is run. It is worth repeating that either of these programs could be easily renamed, so don't think for a moment that running a program with a different name is safe. On the client (controlling) side, NetBus sports an easy to use graphical interface capable of doing many of the same things BO can do. While not hidden quite as well as BO, NetBus is still very difficult to detect and eradicate. A typical virus scanner will usually miss NetBus, so I wouldn't suggest becoming too complacent just because you are running software that attempts to catch virus infected files. As of this writing the developers of BoDetect have introduced a beta version that attempts to detect and eliminate both BO and NetBus. Privacy Software Corporation's BOClean (US$40) is also reportedly able to detect and remove a number of trojan programs. UPDATE (March 2000): One of the better trojan scanners I've come across lately is Backwork from Framework Executive. As of this writing, it can detect and remove 251 trojans and is free for personal use. In addition to a trojan scanner, there are also a couple personal firewalls that appear to work well. BlackICE Defender is available for purchase online (US$39.95). The latest entry into personal firewall protection is Zone Lab's Zone Alarm, which as of this time is free for personal use. While I do recommend using a trojan scanner and firewall, please don't consider these to be substitutes for caution and good judgment. These products can make it more difficult for an intruder to get into your computer, but they can also be defeated if you allow a malicious program to be run, so the rules remain the same: practice safe hex.
First, I am not an expert hacker. I do enjoy watching from the sidelines, but I'm not a player. There could very well be errors on this page and I welcome comments and suggestions from those who know far more than I ever will. However, if you are going to offer corrections, please also offer an explanation or link to a site that backs-up what you are saying. Because your friend HaPpY hAx0r whispered some great secret to you one night in a chatroom doesn't make it a fact. When I publish my comments on the web, I'm going on record as saying that I believe my info is accurate and true, not hearsay and rumors. Please back-up your claims with verifiable data or I can't use it. Second, this page is not a tutorial on how to break into computers, it is intended to make the Internet community aware of the possible risks they face. I believe that factual information plus common sense is your best defense. I included a link to the cDc so you can go there and see what they have to say for yourself. That URL has been published by Ziff-Davis, Wired and ABC News, to name a few. If you have a problem with that then take it up with those organizations first and when they remove their links then I'll consider doing likewise. Don't write and ask me to send you any of the programs mentioned on this page, if you are too much of a lamer to find 'em yourself then you have no business playing with them. Also don't bother sending me an executable file to "try out." If you do that then obviously you didn't read this page very carefully. Send a URL if you want to, but executables are going straight into the bit bucket. I would love to give everyone on the net free tech support... unfortunately I would starve to death in the process (ie. earning a living has to come first). As it is I get over 500 e-mails a month and can't answer most of them, though I do read everything. You are welcome to write or sign the guestbook, but please don't be too disappointed if I don't write back. I usually answer requests for interviews from "real" media sources and would love to be offered a lucrative writing contract (yeah right, dream on, Tom). I encourage you to share this page with your friends. I hope it is helpful and will contribute to keeping the ICQ community a safe and fun place. I have to wonder sometimes when I see sites with a couple of stolen teddy bear graphics and a lame poem that gets a million and a half visitors while pages that offer useful information are for the most part ignored. Do I have to put fuzzy bunnys and colorful balloons on this page before you'll pass it on? If you really want to show what a great friend you are to someone, send them this page... 'cause hugz 'n' kisses won't save their butt from getting probed by a program like Back Orifice, but knowledge will. Okay, enough shameless self-promotion, you get the point. And finally, thank you for visiting. If you have time, look around the rest of the site, there is a lot more to read and see. I also hope you'll bookmark this site and visit again, I try to add something new every month (or two), usually a little lighter than this page. If you decide to leave comments in e-mail or the guestbook, let me thank you now because I really do enjoy reading them and wish I could personally answer everyone. Take care, have fun, make friends and most of all, be careful out there. You may e-mail me at webmaster@diamond-back.com (Please don't send ICQ authorization requests.) Or tell the world what you think of ICQ Hazards by Signing my Guestbook (The Last Word) Subscribe (or Unsubscribe) to the ICQ Lies Update Newsletter If you would like to receive occasional updates about the latest rumors floating around on ICQ, enter your e-mail address in the box and press Send. All info will be kept confidential. (Click here to view our privacy statement.)
visitors to ICQ Hazards. ICQ Hazards Copyright ©1997-2000 Thomas Robert Pasawicz aka DiamondBack All Rights Reserved http://diamond-back.com |